1-877-332-3335|
Toronto, Ontario, Dec. 15, 2016 – Magstar Inc., an ERP software leader in the retail marketplace, has been recognized as a top-20 software vendor in the 2016 RIS News Software LeaderBoard Survey. Outperforming last year’s results, Magstar appeared in the survey’s 25 top-10 categories – with 11 #1 rankings in categories like Leaders in Overall Performance, Leaders in Quality of Support and Leaders in Quality of Service.
“These results are a testament to the trust our customers place in Magstar Total Retail, our ERP software,” said Steven Greenwood, the President of Magstar Inc. “We have been featured as a top vendor for 16 years in a row now and, in that time, it became clear that our customers appreciate more than just our product. They appreciate us – our continued service and commitment to their success. I’m always grateful for the opportunity to be reminded of that.”
The annual RIS Software LeaderBoard survey cuts through the marketing hype and evaluates technology vendors in head-to-head rankings and top-10 lists based on customer satisfaction, i.e. retailer satisfaction.
Retail executives often use these lists to determine which vendors are worth their investment. The top-20 master list is particularly valuable as it shows only the “best-of-the-best” software providers in the marketplace.
“Magstar has been a huge supporter of our business,” said one of Magstar’s clients in their anonymous feedback. “Their ERP system has allowed us to have the visibility to run our business at its optimum potential. The team at Magstar has been there to support our organization. We have implemented our plan on time and on budget.”
This is, of course, not the only retailer to benefit from Magstar’s services. The company helps mid-sized retailers all over North America and the Caribbean by providing 24/7 locally based support from experienced analysts without resorting to call centers.
About Magstar
For 30 years, Magstar has been helping retailers integrate operations and synchronize workflow with omnichannel ERP and POS solutions made explicitly for specialized retailers. With an end-to-end solution that addresses your unique retail needs, you can automate processes, gain inventory visibility and outshine competitors.
Over the past few years, the personal information of millions of credit and debit card users has been jeopardized through data breaches at major retail stores, causing heightened concern and loss of sales. Retail Federations, such as the NRF, claim that the primary reason why credit card data is so easily stolen is because the U.S. financial industry still uses 1960s technology while criminals have quickly adapted to the 21st century. Let that sink in.
Despite retailers’ current efforts and the recent transition to chip-and-PIN cards and EMV-compliant POS hardware, consumers still feel wary about the safety and data security of their credit and debit cards. And we don’t blame them. Just in 2015, it was reported that close to 780 million data records were compromised as a result of 1,632 security incidents. With news outlets constantly spitting out information on retail data breaches left and right, it’s no surprise the possibility of future incidents is top of mind.
Unlike furry key chains, data security is no passing trend for consumers as many believe retailers could be doing more to keep their data secure. Many are willing to go so far as to stop shopping at retailers who are unable to protect their data. This means millions, and we would go so far as to say, billions of revenue down the drain if retailers don’t act and take these concerns seriously.
We came across a recent study conducted by KRC Research in April 2014. The research polled 2,005 Americans ages 18 and over who regularly use one or more credit cards, and was conducted via a 12-minute survey online. Below is a short summary key consumer concerns and what retailers need to do to protect their shoppers and their businesses.
First, let’s begin by summarizing the top consumer data security concerns…
Awareness of recent retail data breaches is nearly universal. Nearly all (9 out of 10) consumers say they have heard about credit or debit card breaches at major retailers over the last several months, with the breaches at Target (95%), Michaels (39%) and being the most memorable. Consequently, these well-known data breaches have impacted sales; Target suffered a 46% drop in profit in the fourth quarter of 2013 that has been widely attributed to its data breach.
This widespread awareness has also had a large and potentially lasting impact on consumer concerns and behaviors. Nearly 7 in 10 report being more concerned about data security now than they were six months ago and 6 in 10 say they are now paying more attention to retail-related data security news. In other words, consumer sensitivity is heightened and major retailers suffering a breach may encounter reputational damage as a result.
Likely as a result of this heightened awareness, only 36% of consumers currently feel extremely or very secure paying with credit cards and only 32% feel the same way about paying with debit cards. This has broad economic implications for businesses, as economic and psychological research has long shown that consumers tend to spend more when paying with credit cards than when paying with cash.
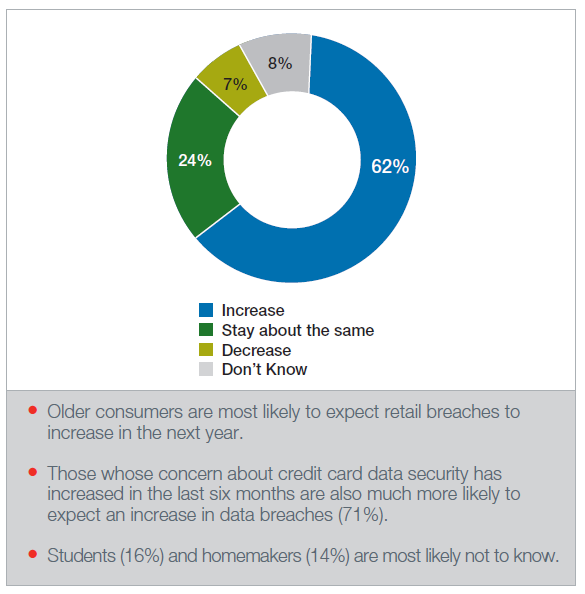
 Unfortunately, few are optimistic about the future of data security. In fact, a majority of consumers (6 in 10) fear that the number of data security breaches such as those that happened at Target and Michaels are going to increase over the next year. This suggests that in order to prevent any further loss of customers, retailers must act quickly and deliberately to inform the public about the steps they are taking to ensure the security of their personal data.
Unfortunately, few are optimistic about the future of data security. In fact, a majority of consumers (6 in 10) fear that the number of data security breaches such as those that happened at Target and Michaels are going to increase over the next year. This suggests that in order to prevent any further loss of customers, retailers must act quickly and deliberately to inform the public about the steps they are taking to ensure the security of their personal data.
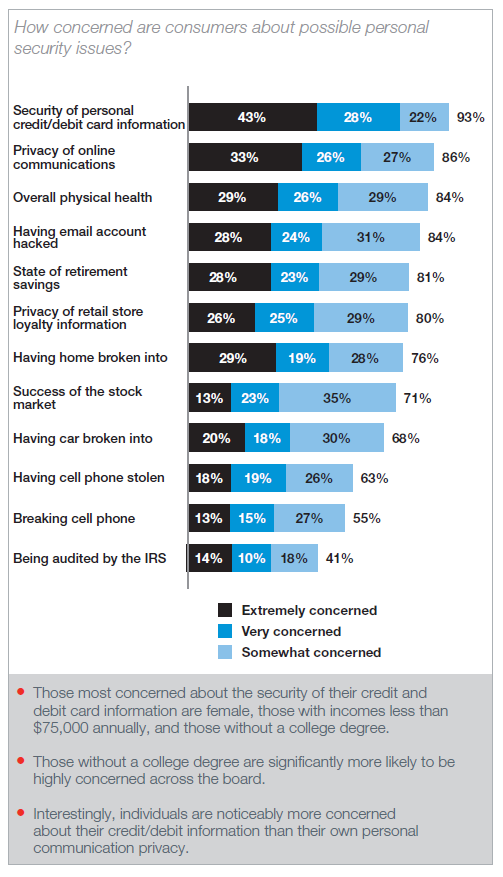
93% of consumers say they are concerned about the security of their personal credit and debit card information. To put this in perspective, that is higher than the number who say the same about the privacy of their online communications (86%), their health (84%), the state of their retirement savings (81%), or losing their cell phone (63%).
Consumers want to know that the retailers they shop at take their data security seriously. 81% of consumers say they would be angry to learn that their favorite retailer was not already using the best available technology to protect consumer credit and debit card information.
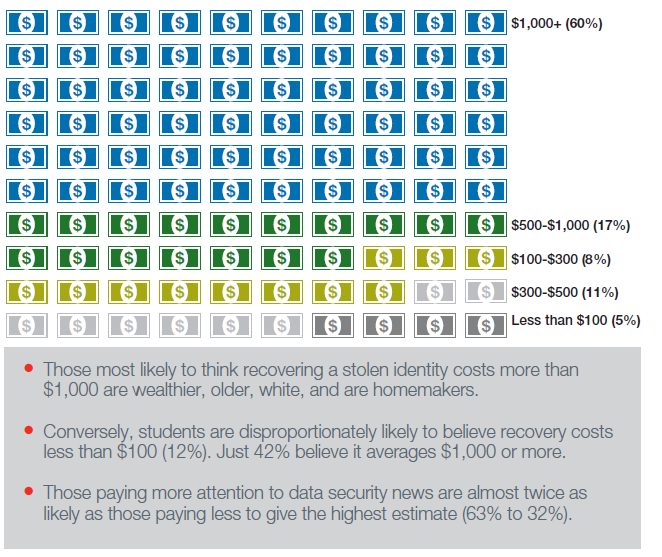
Some of this concern might exist because consumers see recovering a stolen identity as a burdensome and expensive task, with six in ten believing that this process would cost them more than $1,000. With consumers believing this is such an expensive problem, it is even more important for retailers to ensure customer data is as secure as possible.
Consumers are willing to take action to safeguard their data. They report a willingness to change their shopping behaviors by either forgoing credit and debit transactions (76%) or entirely avoiding a particular retailer (38%) if they had personally suffered from a data breach.
Target has experienced the impact of this feeling firsthand: the percentage of US households shopping at the retail giant fell from 43% in January of 2013 (before the breach was made public) to 33% in January 2014, after the news broke.
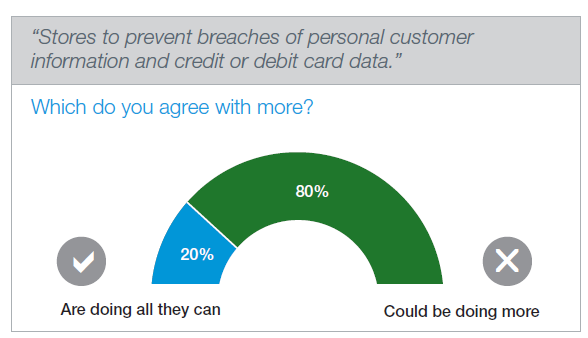
Most consumers hold retailers at least somewhat responsible for the data breaches they experience. An overwhelming majority (80%) think that retailers could be doing more to protect their personal credit and debit card information.
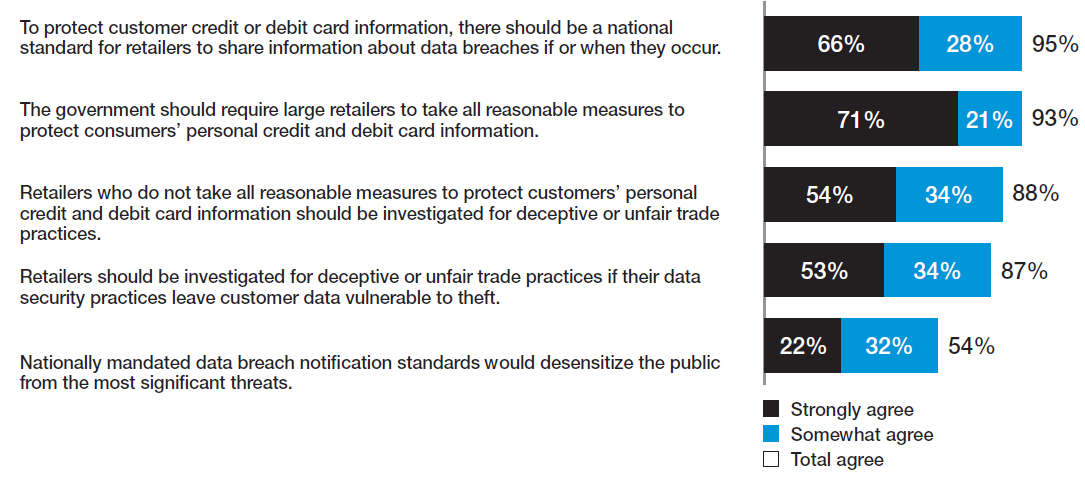
To ensure the safety of their personal information, consumers favor strict regulations on retailers to ensure that breaches are avoided and that all necessary precautions are taken. 95% support national information sharing standards in the event of a data breach. 93% support reasonable government mandated data security safety requirements.
What’s shocking to note is that according to Dark Reading, only 10% of retailers haven’t reported any cyber security exposure in documents filed with the Securities and Exchange Commission since 2011. Even then, only 9% recognize outsourced vendors as a possible threat source and less than 10% have purchased insurance to cover any accidents and exposures. Strictly speaking, retailers don’t seem too concerned with data security.
Simply having solid response measures in place in the event of a data breach may not be enough, according to consumers. They want retailers to be proactive in preventing data breaches, taking steps such as employing the best available technology to secure customer data. One particular solution that consumers see as promising is encryption technology.
9 in 10 consumers see encryption technology as a very appealing service that a retailer could offer to protect consumer data (with 6 in 10 saying it is very appealing). By comparison, only 46% say that fraud and identity protection services are very appealing.
When told about Point to Point Encryption technology, 97% of consumers say that they think it could help protect their information from theft. Consumers are even willing to change their shopping behaviors at retailers that incorporate this technology, with more than 8 in 10 reporting a willingness to shop more frequently at those stores. Half of consumers are willing to pay more for goods and services in return for the peace of mind of knowing their information is secure.
Consumers are looking for more notifications from retailers, with nearly all believing that companies should disclose the occurrence of a data breach to their customers. Most believe this is currently a requirement.
Consumers strongly agree that there should be a national standard for reporting on data breaches and say that the government has a role to play. To a slightly lesser extent, consumers also agree that companies should be investigated for deceptive or unfair trade practices if they fail to protect consumer data.
“Hackers are typically looking for one thing…money; and credit card data means access to money. So, ‘Why is it so hard to protect cardholder data?’ because of a number challenges,” said Vantiv’s Vice President of Security and Risk Products, James Zerfas.
“Cardholder data is operational (authorization requests, data analytics, customer support, settlement, etc.), which means that at some time a person or system will need the data we’re trying to protect. Security and breach prevention would be easier if the only requirement was to protect the data. But, by purposefully ensuring that the data is accessible for operational reasons we are also ensuring that the data is automatically more vulnerable,” James continues.
Additionally, “systems are dynamic, not static, and logistically difficult to manage across multiple locations that span towns, states, regions, and even countries. Once a vulnerability is discovered, the ability to address it consistently and instantaneously is inherently problematic.”
James concludes by stating “not all risk is systematic; there will always be a human element… cameras, external skimmers, bad policies, poor training, fraudulent employees, are all non-systematic ways cardholder data is lost.”
Retailers beginning to focus on data security can start by establishing an in-depth security strategy and by creating a workplace culture of innovation. “There are two key factors which must be taken into consideration when protecting customer data: infrastructure planning and employee education,” said Kevin Glendenning, President at Starnix Inc.
All employees must be trained and educated in creating effective passwords, using the network safely, and in dealing with personally identifiable information. “It is also important that all systems and devices in a company’s infrastructure be kept up to date with security patches and advisories, however, this alone is not enough. Businesses must be proactive with emerging technologies as threats evolve. Target’s use of 3DES encryption, for example, played a key role in allowing attackers to bypass their encryption through a series of brute force attacks in 2014,” continues Kevin.
“Beyond the technology, infrastructure architects must also plan their implementations with security in mind. Home Depot found itself in an unfortunate situation in 2014 when attackers leveraged a compromised third-party vendor account to ultimately install malware on the retailer’s self-checkout machines. Access to mission-critical systems should only be given to those who need it, and only to the level necessary for their specific role; this is especially true when third-parties are granted access to internal systems.”
 “Employees and vendors with access to sensitive data must be educated on the dangers of “social engineering.” Humans with access to critical systems remain the weakest link in the chain and represent an easy entry point for attackers, regardless of the security state of the systems.”
“Employees and vendors with access to sensitive data must be educated on the dangers of “social engineering.” Humans with access to critical systems remain the weakest link in the chain and represent an easy entry point for attackers, regardless of the security state of the systems.”
– Kevin Glendenning, President of Starnix Inc.
Instead of allocating thousands or millions of dollars towards legacy systems, retailers need to consider investing in new technology with built-in security protocols and authentication systems. “Retailers with legacy software and hardware should ideally replace them. However, for legacy systems this is usually easier said than done. It is not uncommon for a company to rely on a piece of proprietary software that was written years ago (possibly even a decade or more). It was developed to meet a certain need at the time, and the developers have since moved on,” said Kevin.
 “One consistent gap is that most infrastructure is inconsistent. Maintaining systems over time usually results in different vendors and different versions of hardware and software, which introduces complexity, varied capabilities, and inconsistent behaviors resulting in additional risks,”
“One consistent gap is that most infrastructure is inconsistent. Maintaining systems over time usually results in different vendors and different versions of hardware and software, which introduces complexity, varied capabilities, and inconsistent behaviors resulting in additional risks,”
– James Zerfas, Vice President of Security and Risk Products at Vantiv.
“If replacing your legacy software or hardware with a modern solution is not feasible today, then you must take every step available to protect that device. Understand and acknowledge that it is extremely vulnerable to attack, and adjust your infrastructure accordingly to limit access to the device as much as possible,” continues Kevin Glendenning.
Retailers should also consider implementing analytics-based security tools that can identify anomalous behavior in real-time and report this information to designated users for further investigation.
All network points must also be secured including POS terminals, e-commerce websites, third-party vendor links, and any mobile handheld devices used by retail employees.
“Look for ways to remove data from your systems and if needed (for operational reasons), look for solutions like Point-to-Point Encryption and Tokenization that leverages the use of non-sensitive, surrogate values for these tasks,” said James Zerfas.
“Point-to-Point-Encryption at the POS is the process of encrypting card data at the point entry, specifically a credit/debit pin pad is injected with an encryption key which the pin pad uses to encrypt the captured card data immediately. The PIN pad then sends that transaction information to the processor with the encrypted data and the processor will then decrypt the card data at the other end,” explains Naftali Nathan, Head of POS at Magstar.
 “Using a P2PE solution ensures that card data cannot be accessed from the retail location’s network, there is no card data being sent just random numbers. It also reduces PCI exposure; your entire network is no longer in scope for PCI, as well as reduces the amount of PCI paperwork required to be filled out every year. P2PE removes the threat of exposure from the Retail Operations.”
“Using a P2PE solution ensures that card data cannot be accessed from the retail location’s network, there is no card data being sent just random numbers. It also reduces PCI exposure; your entire network is no longer in scope for PCI, as well as reduces the amount of PCI paperwork required to be filled out every year. P2PE removes the threat of exposure from the Retail Operations.”
– Naftali Nathan, Head of POS at Magstar
James Zerfas ties it all together: “A great posture for any business is that getting breached is a matter of time, but make sure that what the criminals get access to can’t be used to commit fraud.”
Retailers are easy prey for hackers. There is no need to rob a store when it’s easy for an opportunist to get into a system, get what they want, and get out without being caught. One of the first steps of dealing with retail security challenges is acknowledging their destructive potential and recognizing that no business is truly safe. Incorporating a data security strategy into existing business plans should be a top priority for retailers of all sizes.
Protect your data, protect your customer, and protect your business.
To download the full summary report of the research findings, please click here.
Instead of the customer coming to you, why not show up on their doorstep? Many brick-and-mortar retailers have implemented a mobile retail presence to ensure that they are always in the middle of the action.
For retailers with mobile stores or those considering this service, there is one very important question to answer:
“How on earth do I manage my mobile stores like I manage my brick-and-mortar locations?”
Good question. Our customer, Mister Safety Shoes (MSS), recently discussed how they addressed this concern in an interview with Innovations Magazine. In this brief blog post, we will summarize a few key takeaways for mid-sized retailers.

Over the last 40 years, Mister Safety Shoes expanded to 16 brick-and-mortar locations and 17 mobile stores across Canada. Before overhauling their legacy ERP and POS solution, MSS experienced challenges in managing their mobile stores’ inventory, customer information, and equipment eligibility program. This involved a manual and laborious effort in replenishing inventory, which often resulted in mistakes made due to human error.
Up until 2010, their brick-and-mortar stores were still placing replenishment orders via fax machine! Of course, this type of process can lead to misplaced invoices and additional steps associated with end-of-day procedures. In the event that inventory went missing, Mister Safety Shoes risked putting a worker’s life in danger by not providing them with the safety equipment they need.
“There was a great deal of human element involved with the picking process, which meant back orders were not always being tracked.”
-John Colantonio, Managing Director of Mister Safety Shoes

Mister Safety Shoes took a hard look at their current infrastructure and soon realized that enough was enough. Gaps in communication, manual tasks, and recurring errors were just the tip of the iceberg. This led the company to search for a solution that could help them solve their problems.
Do any of these issues sound familiar? Retailers with similar business profiles must have a detailed understanding of their pain points before making a transition. A good place to start is our ERP Selection Checklist.

It can often be overwhelming to analyze various software solutions. For this reason, many retailers, such as Mister Safety Shoes, start by reaching out to their network and asking for recommendations. After all, we are more likely to trust the experience of a customer rather than the word of a brand.
After an elaborate gap analysis and numerous demos, Mister Safety Shoes chose Magstar Total Retail, including Total POS, Total Warehouse, Total CRM, and mobile handhelds for the warehouse. This enabled them to reduce manual data entries, email invoices, track inventory levels at all stores, and efficiently replenish mobile and brick-and-mortar stores. By replacing their legacy software, Mister Safety Shoes can now rely on Total Retail to rotate the gears in the background, all the while providing superior customer service, no matter where their mobile stores take them.
A flexible ERP solution can help retailers reduce human error and keep money in their pockets. There may never be a perfect time to make the switch from a legacy ERP, but retailers in the research stages need to take their time to find the ERP solution that’s right for them.
MILPITAS, Calif. — June 07, 2016 — Elo, a global supplier of touchscreen solutions, today announced Magstar Inc, provider of enterprise resource planning (ERP) retail software, has certified Elo’s X-Series and E-Series touchscreen computers for use with its award-winning retail software suite. This certification delivers the combined benefit of decades of development and innovation for retail point of sale (POS) software and hardware from Magstar and Elo.
Operating a successful retail business today demands a sophisticated technology solution. Retailers expect their technology solutions to support multiple in-store digital touchpoints with functionality such as self-serve payment, loyalty program management, product scanners and powerful analytics. Magstar’s certification of Elo touchscreen computers ensures retailers benefit from Elo’s flexible modular design, convenient serviceability, long life cycle, maintenance, and support. This backend software will help with business efficiencies and seamless omnichannel experiences.
“We’ve certified Elo, understanding the value the robust retail hardware portfolio will provide our customers,” said Steven Greenwood, President of Magstar. “Retailers looking for an affordable, feature-rich POS terminal with a modern look and interactive capability will love this full solution.”
The flexibility of the Elo hardware platform allows partners and customers to choose their operating system. Magstar operates on Linux, a supported option for Elo’s certified E- and X-Series touch computers:
“Elo continues to enable in-store innovation with a robust portfolio of interactive touchscreen displays and computers,” said Craig Witsoe, CEO of Elo. “Partners like Magstar rely on our quality and eye to future innovation to enhance the experience at the point of sale and through every fixed digital touchpoint in store.”
Magstar provides intuitive ERP software with built-in POS, CRM and loyalty programs, retail business intelligence, mobility solutions and supply chain support for a variety of mid-sized retailers, including wine and spirits, drugstores, pet stores, apparel, and jewelry. Elo hardware integrates with common peripherals for card-swipe, EMV, scanners and more, making it easy to implement a fully integrated hardware solution from the Elo portfolio.
About Elo
Elo is a global leader in touchscreen solutions, including modern point of sale systems. The inventor of the touchscreen, Elo now has 20+ million retail and hospitality installations in 80+ countries, with products designed in California and built to last with a three-year standard warranty. The Elo touchscreen experience has consistently stood for quality, reliability, and innovation. Elo intellectual property is protected by global patent, trademark. and design registrations. Learn more about Elo’s POS solutions at EloTouch.com.
About Magstar
For over 30 years, Magstar has been offering out-of-the-box, industry-specific ERP solutions to mid-sized, multi-location retailers across North America. Magstar TOTAL Retail is an award-winning omni-channel solution that covers the entire operation from store front through to warehouse and head office. We understand the fact that no two retailers operate the same way, and we will work with customers to further customize the solution to meet their specific business needs. Learn more about Magstar’s solutions at Magstarinc.com.
 Making the decision to invest in a new point of sale system for your retail chain is committing to a major purchase. When selecting both the software and the POS hardware, retailers have to be attentive to how good of a fit the package will be, both now and years into the future. The ideal point of sale hardware will suit a retailer’s needs for many years after the initial purchase, and will also have a physical longevity that ensures it doesn’t need to be repaired too often or replaced too soon.
Making the decision to invest in a new point of sale system for your retail chain is committing to a major purchase. When selecting both the software and the POS hardware, retailers have to be attentive to how good of a fit the package will be, both now and years into the future. The ideal point of sale hardware will suit a retailer’s needs for many years after the initial purchase, and will also have a physical longevity that ensures it doesn’t need to be repaired too often or replaced too soon.
There is a lot of conventional wisdom and many new trends to consider when selecting the hardware for your point of sale. The common considerations are things like cost, support, mobility, and ease of use. These are all extremely important check boxes to fill as a retailer is doing their research and learning about all of their different options. Any number of guides and articles can assist with the core questions of what a retailer looking to buy point of sale hardware ought to be asking.
Sometimes, however, this means that some of the more obscure considerations get overlooked. There are a few insider secrets for getting the greatest value out of your point of sale hardware, planning for a setup that will last longer and cost less. That inside knowledge on retail hardware, direct from thirty years of experience working with a wide variety of hardware suppliers in the industry, translates into some questions that retailers can be asking to make even more informed decisions.
At first glance, it seems self-evident that a better processor in a point of sale means faster CPU and therefore better performance. Investing more money into the processor for your hardware should provide an equivalent return in the usability and functionality of your point of sale.
That isn’t necessarily the case. Ten years ago, the more processing speed you had, the better. Technology today, however, has reached a point of diminishing returns. The difference between a mid-tier processor and a top-tier processor in a piece of retail hardware is really no longer distinguishable, because the mid-tier is already so good. The thing to remember is that the highest level of technology available is largely intended to be used for tasks like running graphics-intensive video games, or editing and compressing creative projects like large video and audio files. These are demanding tasks for a computer that really benefit from the best CPU – and it’s quite unlikely a retail POS will ever need to do anything quite so intensive.
In some ways, going to the most expensive processor available for your POS hardware is a bit like installing a jet engine into a midsized sedan: with what you need that car to be able to do, you really don’t need that kind of power, and ultimately it just weighs the whole car down without providing any tangible benefit.
In fact, having a faster processor in a device that doesn’t need it can negatively impact performance. Especially in more compact devices, the extra power of the processor means that the hardware runs at a higher overall temperature, which can reduce performance, lower battery life, and in extreme cases cause crashes. So not only do you not see much improvement for the increased cost of the more expensive processor, sometimes it actually provides worse performance than a mid-tier processor would in the same hardware.
Knowing how long a piece of hardware will last can be difficult to determine. All hardware suppliers will make ambitious claims about the longevity of their products, and all will say they’re designed for durability in the retail environment. For retailers who want to invest time into ensuring they’re making educated, informed choices and not missing any pieces of the puzzle on which hardware will best suit their needs, it can be valuable to seek out third-party studies of hardware performance.
The importance of durability is obvious – there’s no sense in investing in hardware that won’t last a long time or will need frequent repairs. Any downtime of your POS negatively impacts customer experience and sales, so retailers should exercise due diligence in choosing hardware that will be reliable and long-lived. When a hardware vendor claims their product is durable, retails should ask specifically about:
Many retailers are unaware, for example, of the large role that dust accumulation plays in hardware failure. Hardware supplies know this and go to efforts to dust-proof their designs, but some do it better than others, and this shows in lab-tested studies that determine how well hardware continues to perform in highly dusty environments like retail stores. If dust does manage to accumulate inside the POS device, this raises its overall operating temperature which, as mentioned before, decreases performance and increases the likelihood of a hardware-related crash.
Not all hardware has been specifically built to serve as a point of sale, and not all point of sale hardware has been specifically built to serve retailers. There are some suppliers who use the same hardware for all sorts of enterprise hardware setups, succeeding by being generalists with largely multi-purpose technology. Whether this should matter to retailers is some subject of debate, but it’s worth being aware of the differences so that the individual retailer can make that call themselves instead of making a purchase with the false belief that all point of sale hardware is purpose-built for retail.
Hardware makers who focus in on the retail vertical are more likely to be paying attention to and investing into concerns like dust-proofing, how design impacts customer experience, and physical integration with printers, scanners and payment processing devices. Point of sale hardware derived from non-retail technology can tend to look old and boxy, or corporate and bland. For retailers seeking more modern, aesthetically pleasing hardware, it can help to be aware which of the suppliers are generalists and which ones architect specifically for the retail experience. If design isn’t a major priority, the question of suitability for the retail environment in terms of performance should still be important to the retailer. Making a point of asking whether the device is purpose-built for retail can turn up some good information that will help in making a final decision.
There’s a limit to what can be gained from online research. Ultimately, the best way for a retailer to ensure they’re making the best possible match with their POS hardware and software is to make a connection with an expert in the industry willing to be a consultative partner that speaks from experience and is willing to talk frankly about the strengths and weaknesses of all options available to the retailer. A good software vendor with a large number of hardware suppliers will bring a highly informed and largely unbiased opinion to the table when talking about the pros and cons of each system.
Before committing to any one set of hardware, a retailer should feel totally confident that they have all the facts and know exactly what they’re looking for.